Abstract
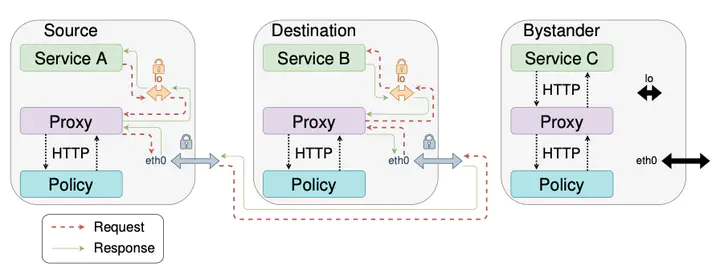
Data leaks and breaches are on the rise. They result in huge losses of money for businesses like the movie industry, as well as a loss of user privacy for businesses dealing with user data like the pharmaceutical industry. Preventing data exposures is challenging, because the causes for such events are various, ranging from hacking to misconfigured databases. Alongside the surge in data exposures, the recent rise of microservices as a paradigm brings the need to not only secure traffic at the border of the network, but also internally, pressing the adoption of new security models such as zero-trust to secure business processes. Business processes can be modeled as workflows, where the owner of the data at risk interacts with contractors to realize a sequence of tasks on this data. In this paper, we show how those workflows can be enforced while preventing data exposure. Following the principles of zero-trust, we develop an infrastructure using the isolation provided by a microservice architecture, to enforce owner policy. We show that our infrastructure is resilient to the set of attacks considered in our security model. We implement a simple, yet realistic, workflow with our infrastructure in a publicly available proof of concept. We then verify that the specified policy is correctly enforced by testing the deployment for policy violations, and estimate the overhead cost of authorization.