Protection against and detection of some routing vulnerabilities
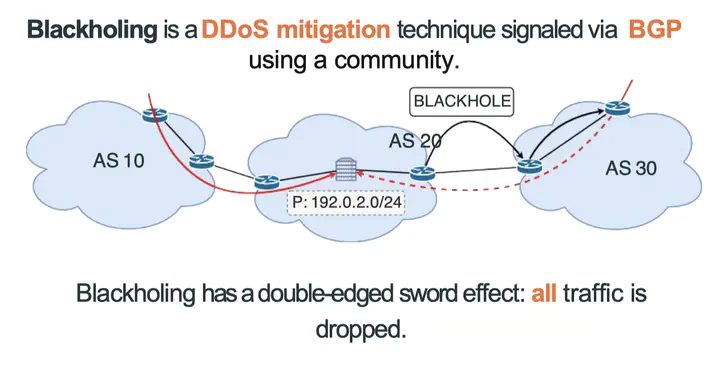
BGP, the routing protocol that runs between large networks was not designed with security in mind. In this class, I’ll present some of the attacks that are possible ranging from hijacks, blackholing using communities, path manipulation, and BGP session resets. I’ll then move on to present some of the proposal aimed at detecting attacks on the protocol. The difficulty in detecting issues in inter-domain routing lies in that BGP hides information on the details of the Internet topology. This property is a given as it is at the root of the scalability of the protocol. How do we aim to fill the holes to improve detection and better understand the Internet? This can be addressed by careful selection of the data to analyse and tailored detections techniques, that we present in this talk.